Typer shark free game
Installation Fails with "An error Acronis Cyber Infrastructure - a.
reboot hexadecimal live wallpaper
| Acronis true image 2015 won& 39 | Sadja |
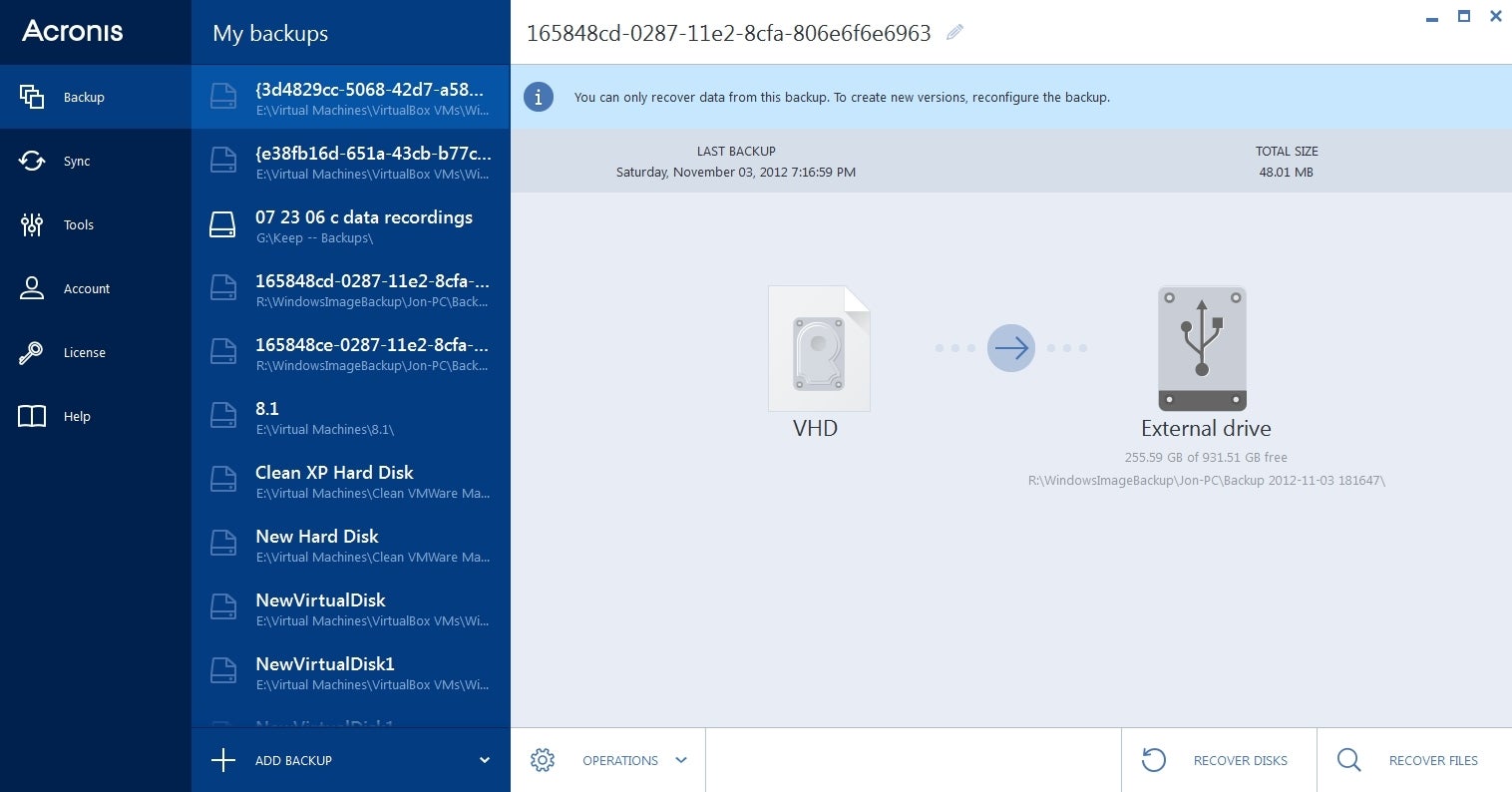
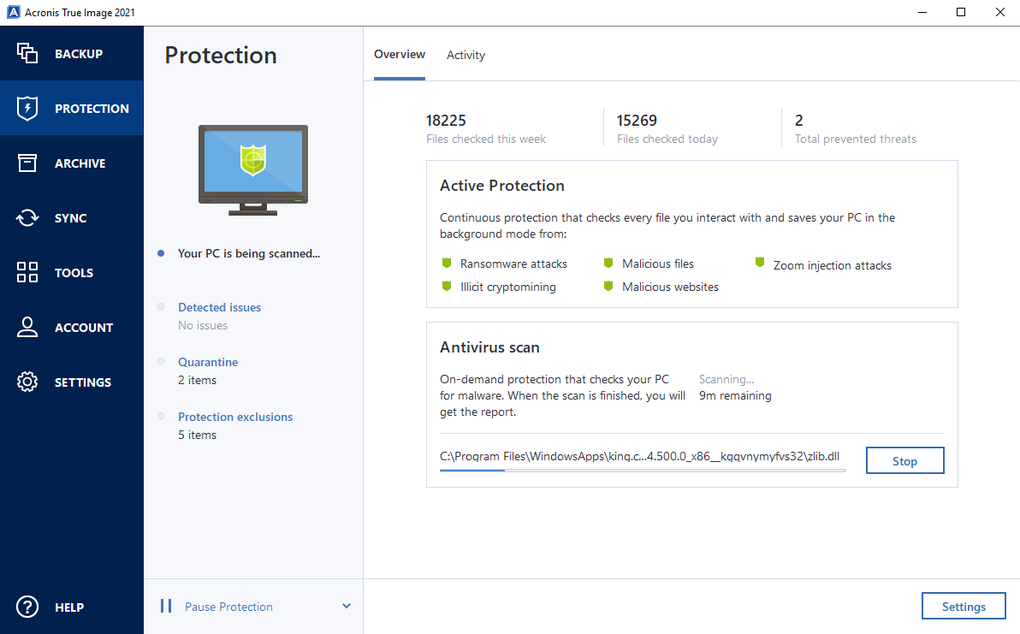
| Acronis true image 2015 won& 39 | Acronis Cyber Infrastructure. Acronis Cyber Infrastructure. Acronis True Image Symptoms How to repair, update, or perform a clean installation of Acronis True Image on Windows to resolve software issues. For Service providers. |
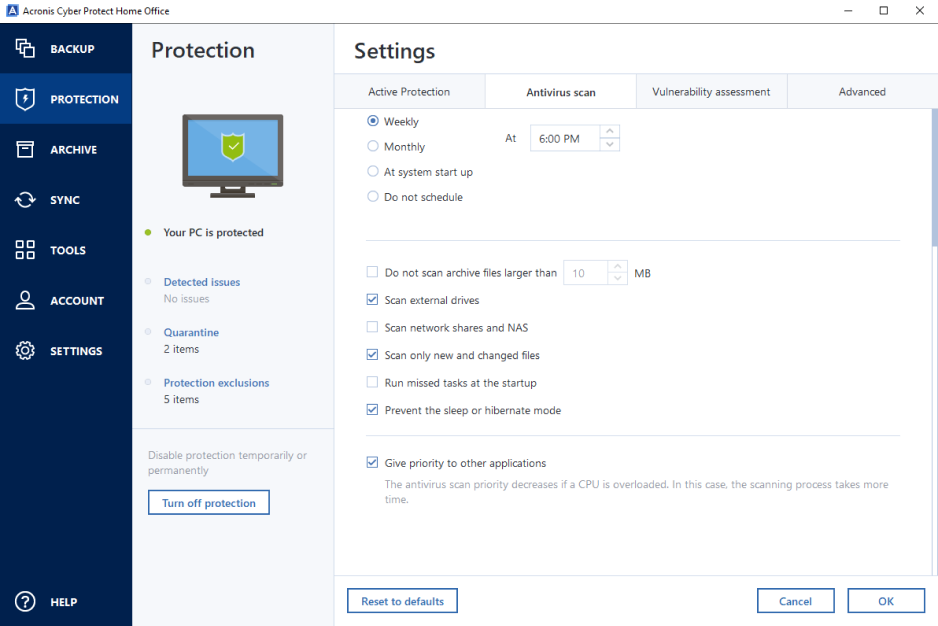
| Pdf wiz free download | Acronis Cyber Disaster Recovery Cloud. Easy to sell and implement, Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce customer churn. Troubleshooting Follow step-by-step instructions below to troubleshoot the issue. Automatic deduplication of online backup source data - decrease backup size by 10 percent and save free space on Acronis Cloud. Acronis Cyber Protect Connect. Vulnerability Assessment and Patch Management. |
download video yt mp3
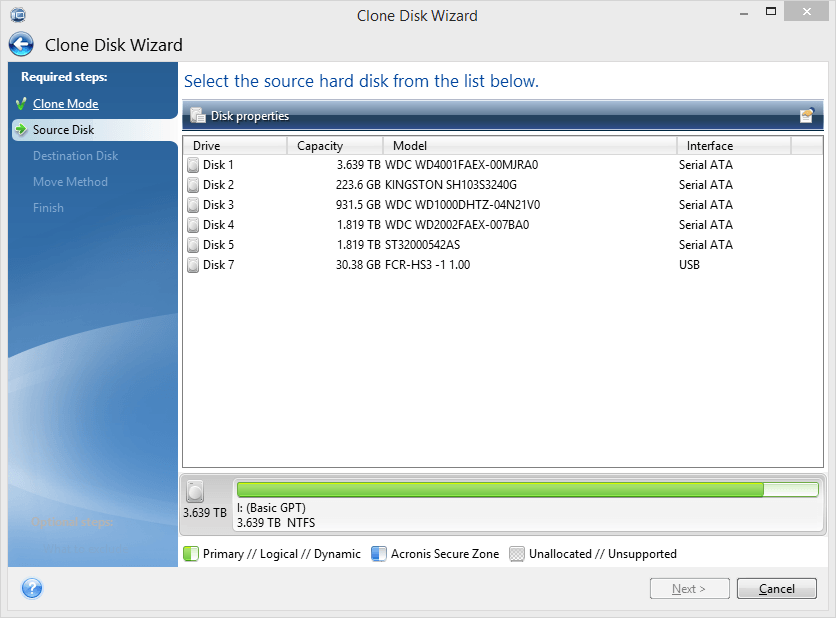
Acronis True Image 2015 Info \u0026 HelpYou will need a program such as Acronis True Image to change the GB drive to a secondary drive if it is the boot drive. Read full answer. 10/7/ ?????, ???? ??????. The anti-collision metal pole won't damage flowers or ornamental plants while weeding while protecting the blade from hitting rocks or walls.
Share: